- Launch Kali Linux
2. Search in application named ‘ Nmap Zenmap ‘
3. Nmap – Zenmap window GUI appears
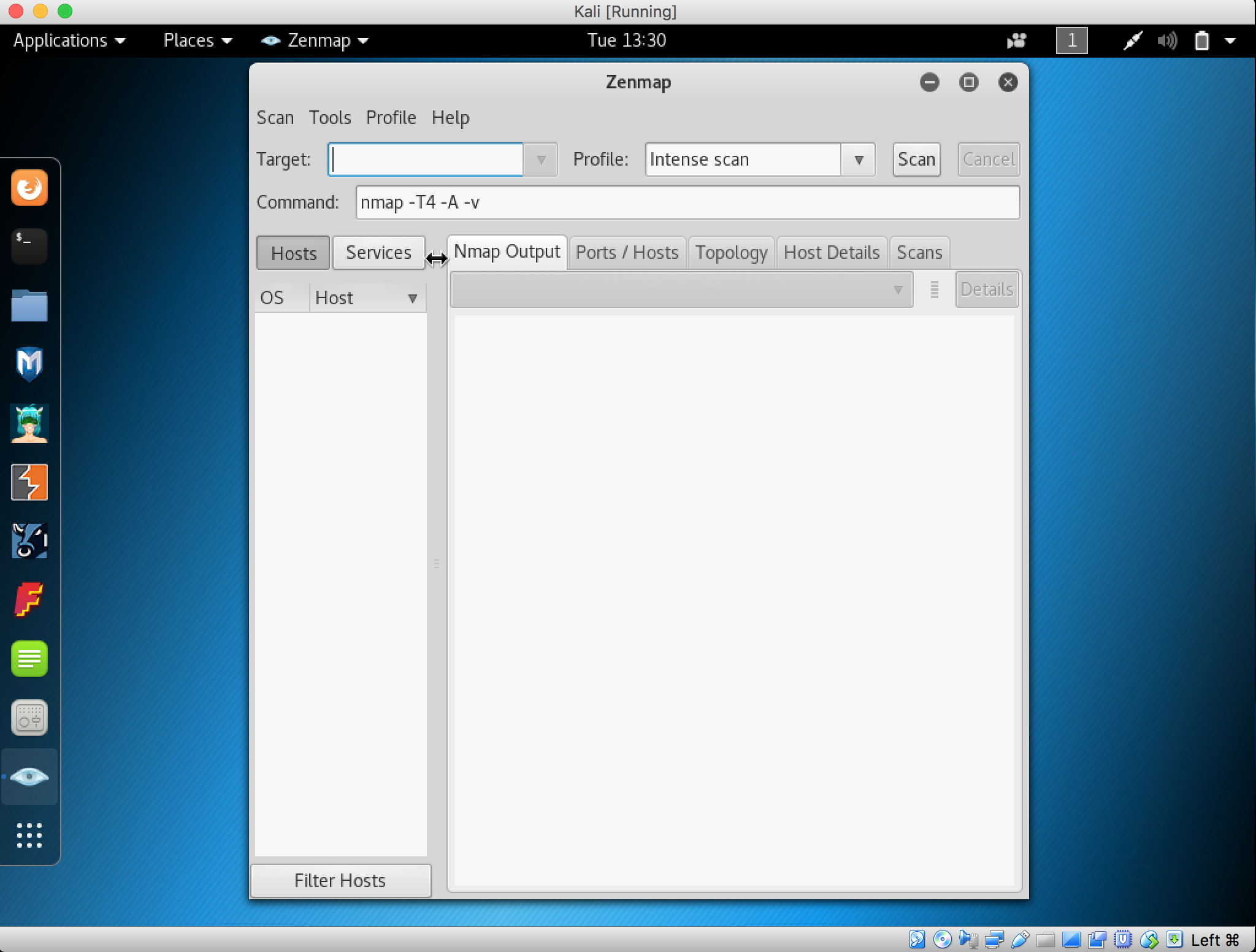
4. Fill the IP target, choose Intense Scan and press the Scan button then nmap will start scanning the IP
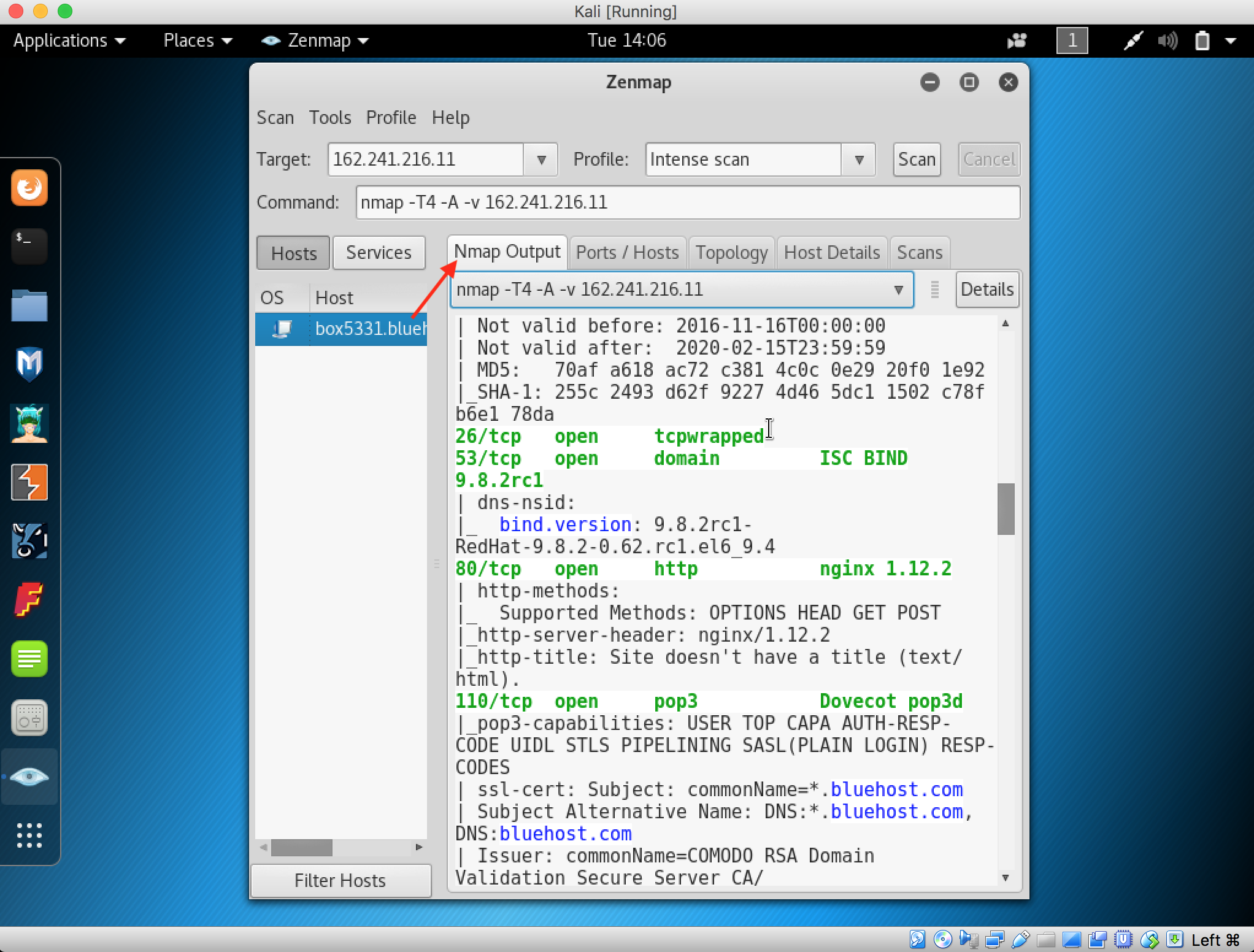
5. Nmap shows the result of the scanning
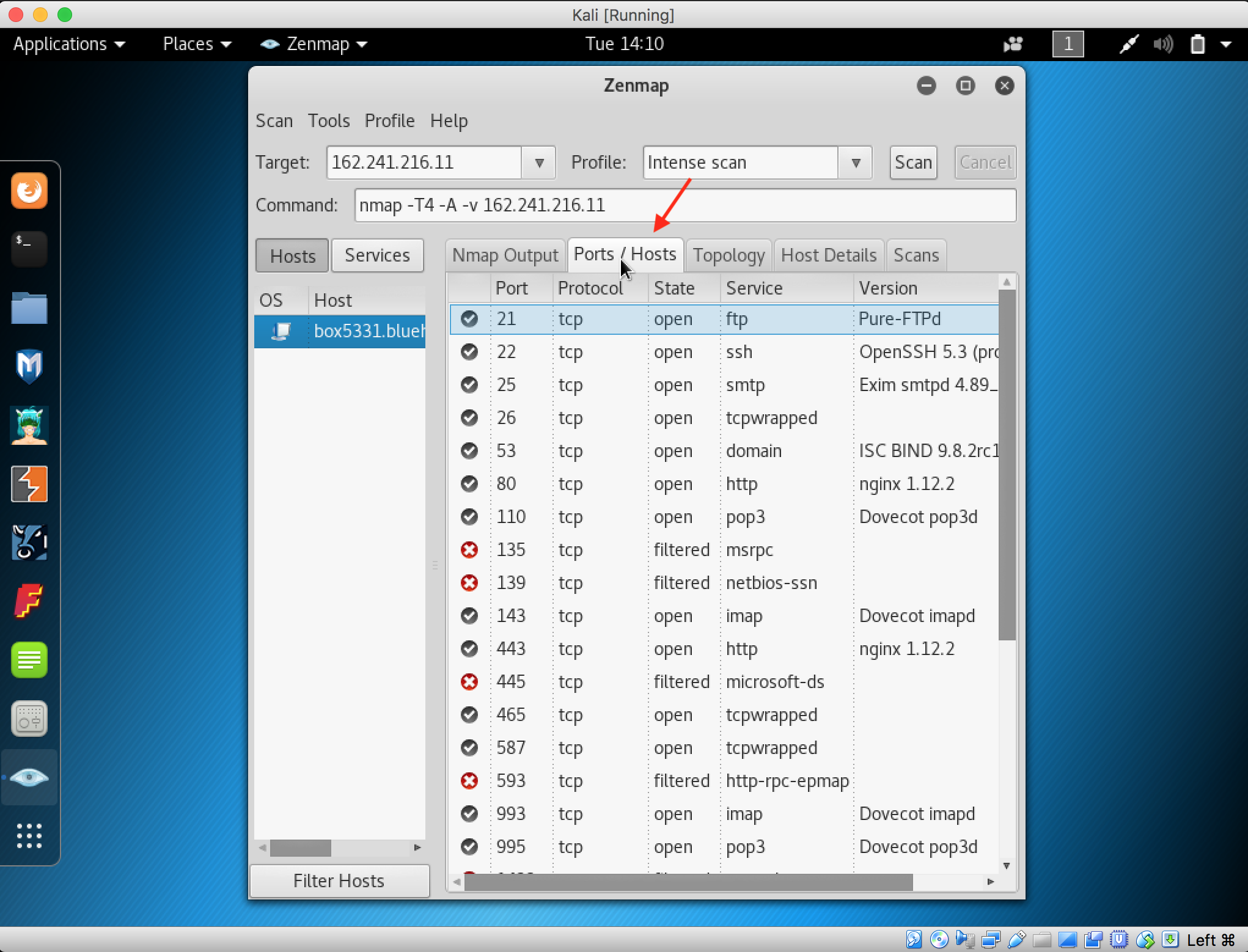
6. Click the Ports / Hosts tab to show more information
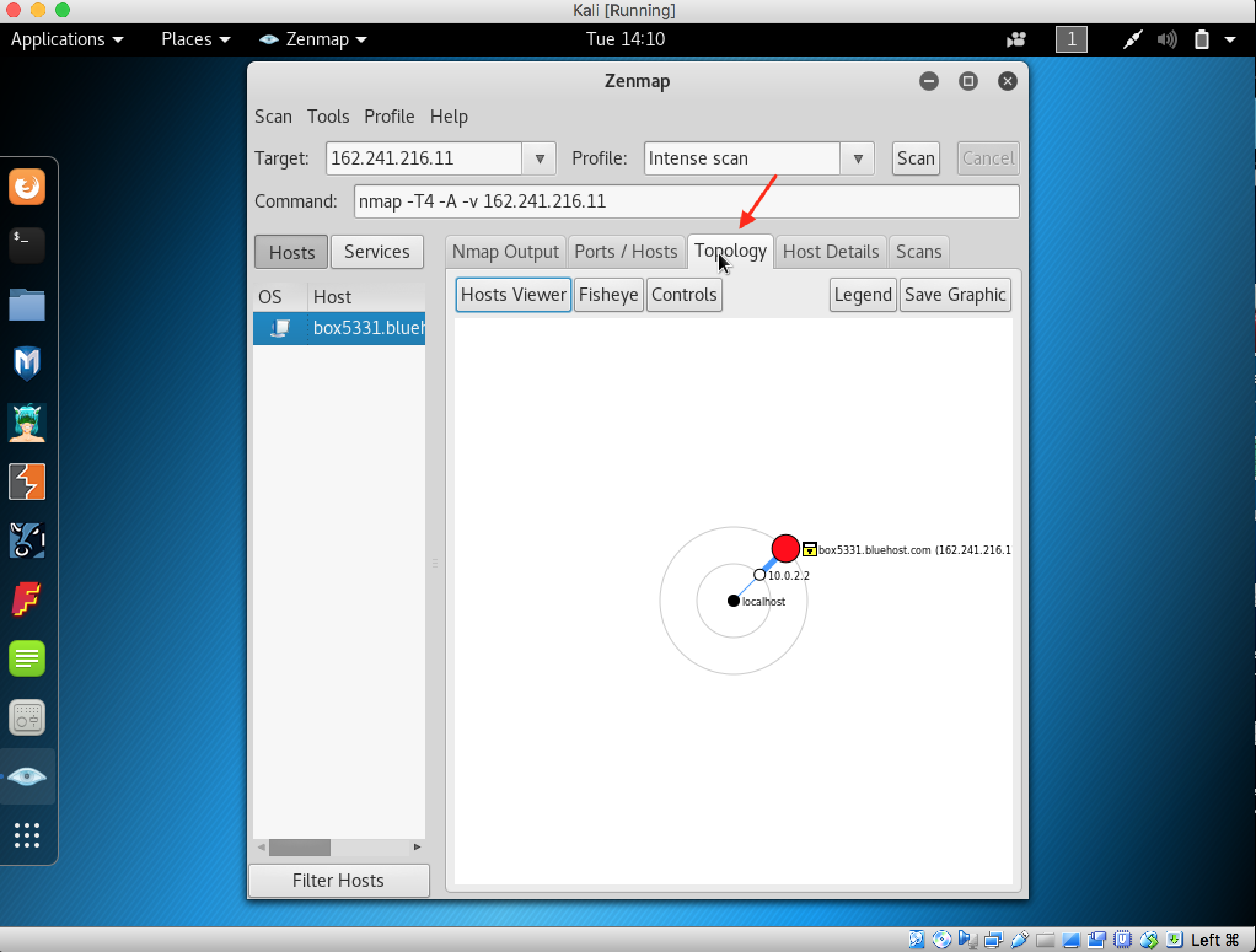
7. Click the Topology tab to view Nmap’s topology for the provided IP address in the Intense scan Profile.
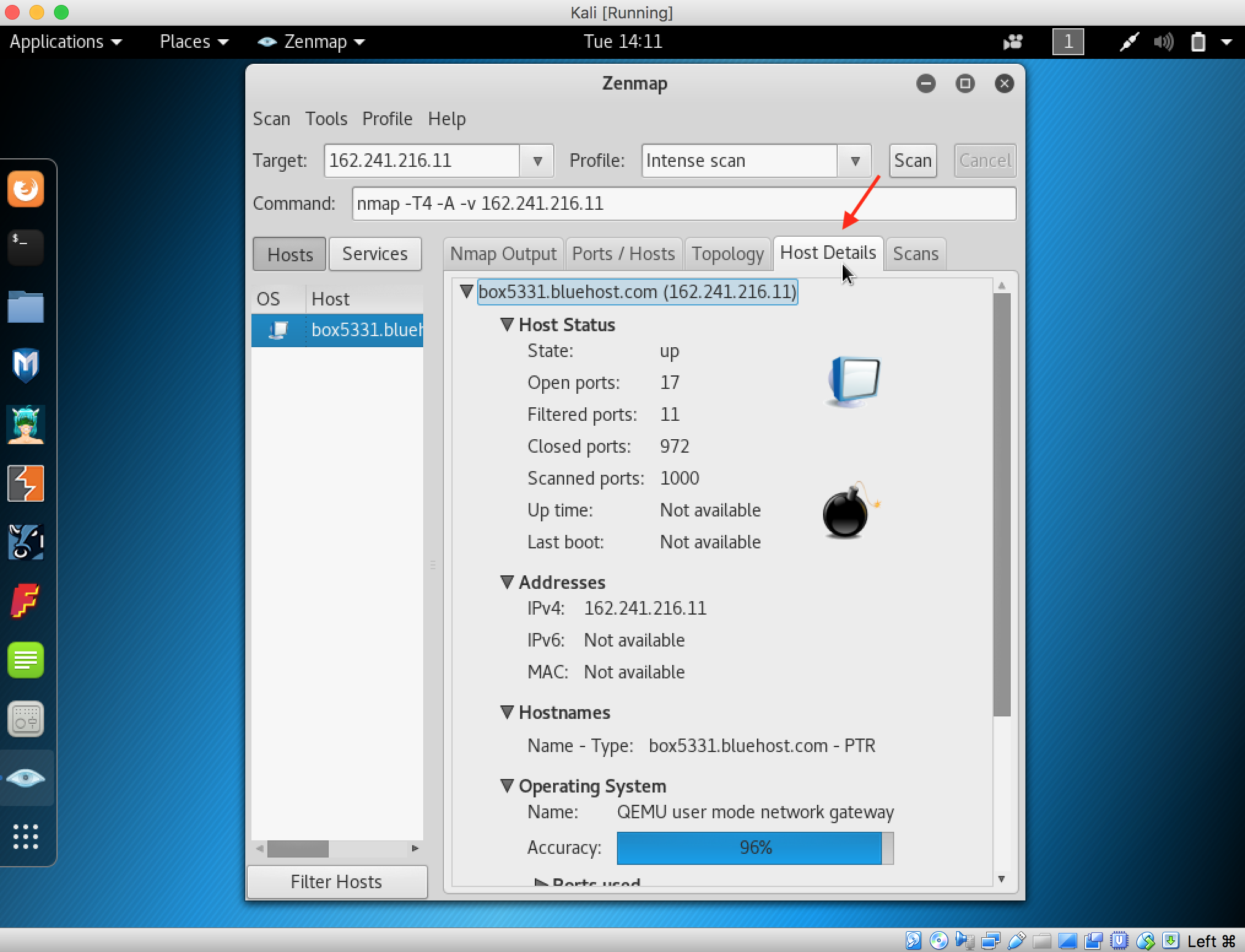
8. Click the Host Details tab to see details of all hosts discovered
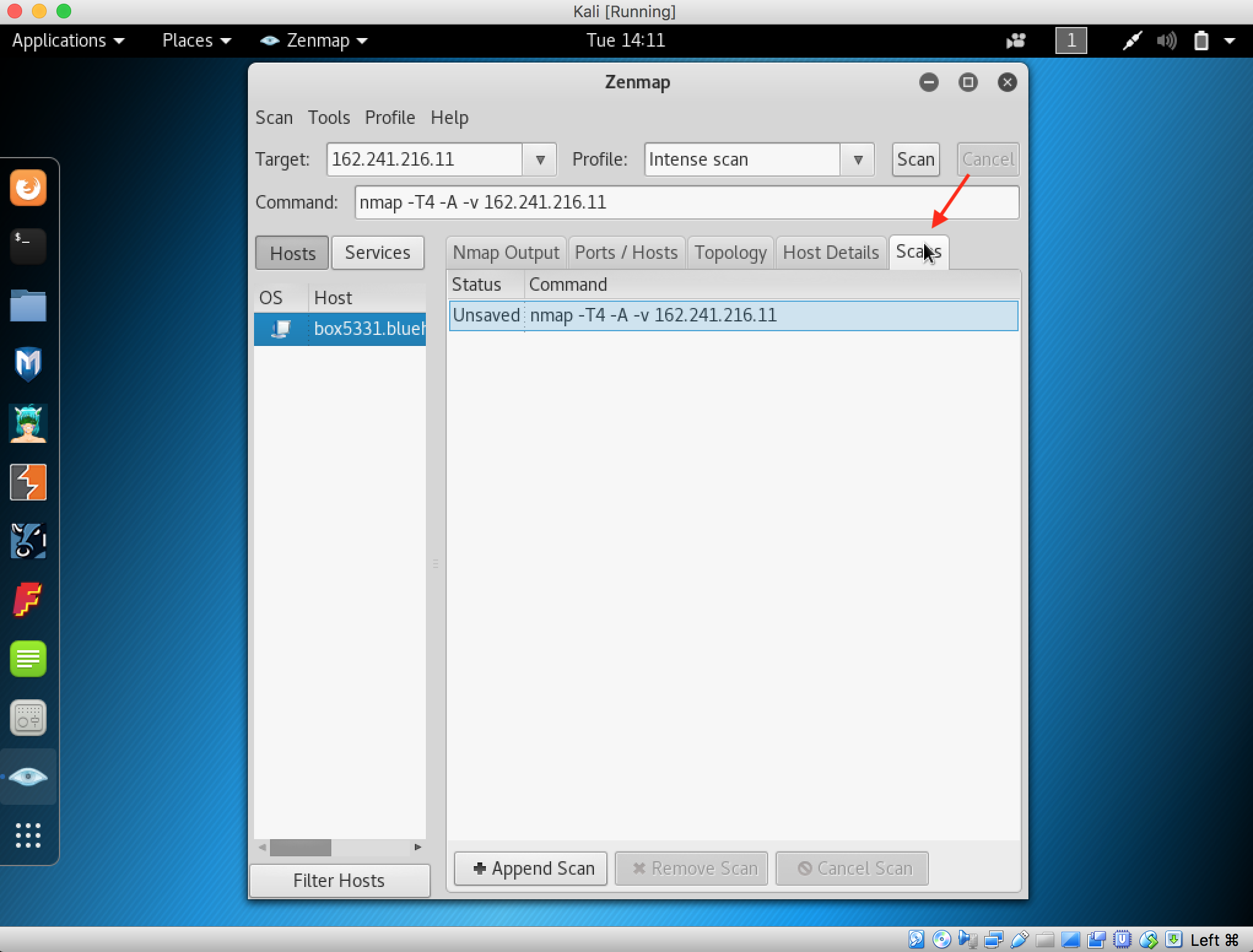
9. Click on the Scans tab to see scan detail for the IP
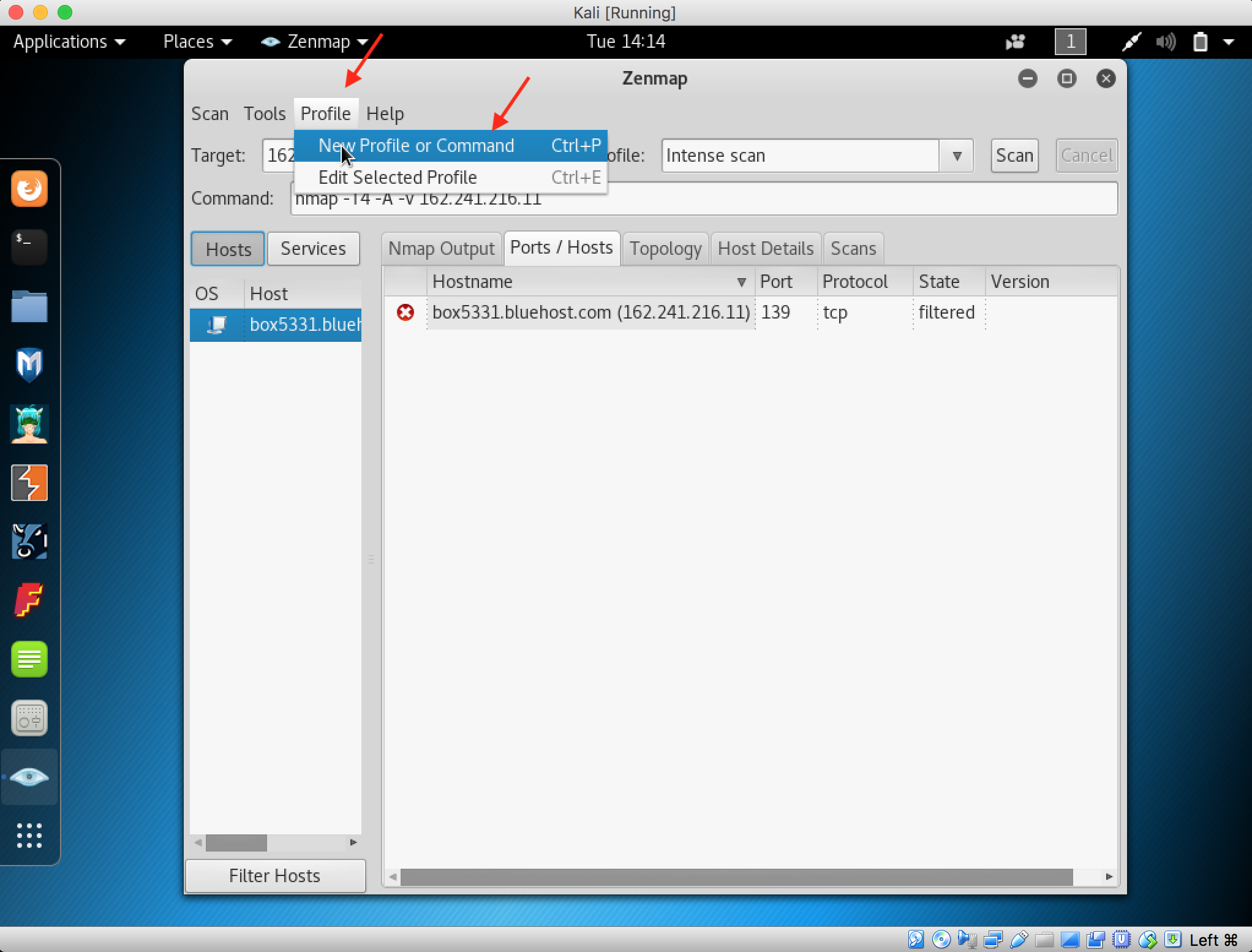
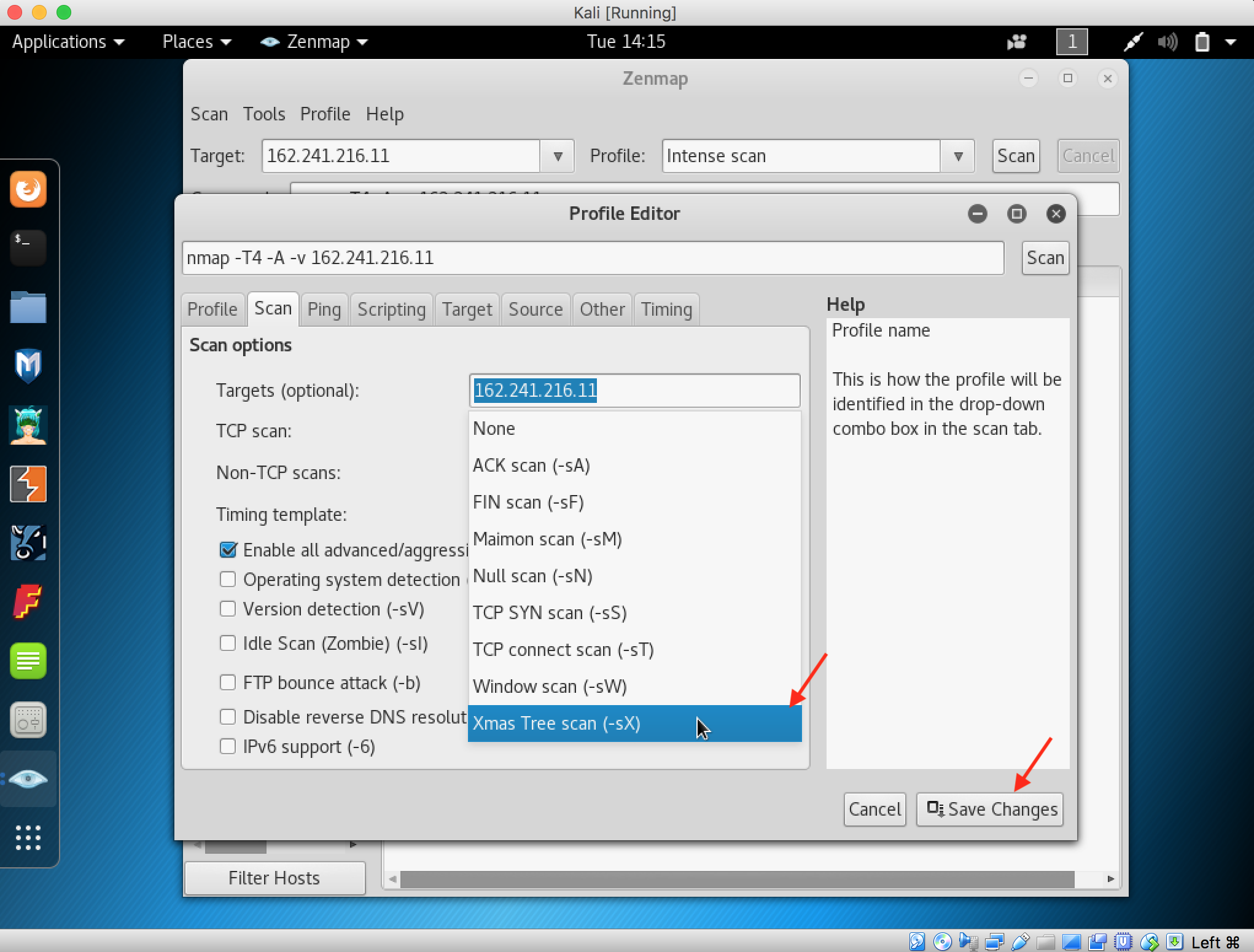
10. Xmas scan sends a TCP frame to a remote device with URG, ACK, RST, SYN, and FIN flags set. To perform a Xmas scan, create a New Profile
11. Select the Profile tab and fill the name with Xmas Scan
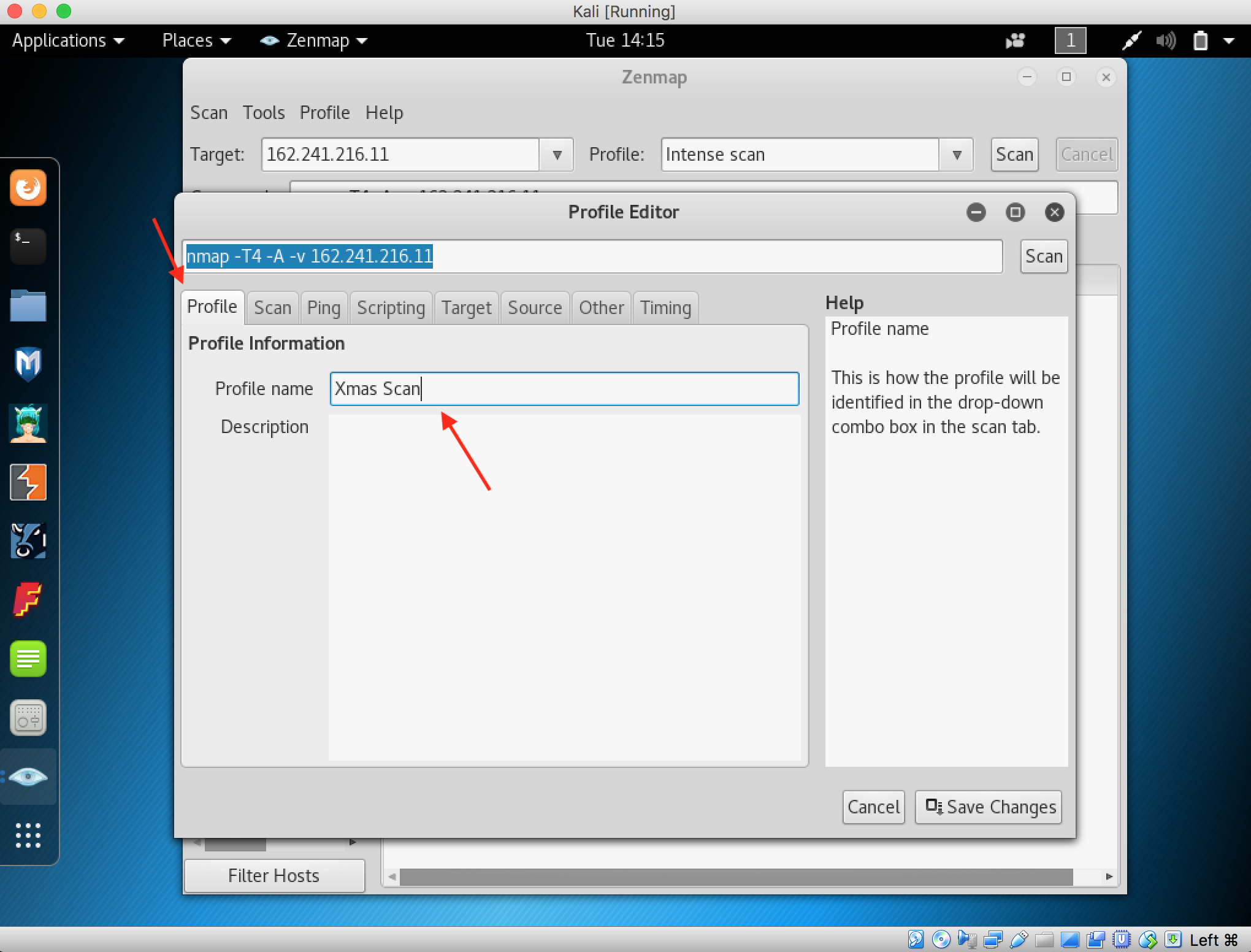
12. Click the Scan tab and select Xmas Tree scan (־sX) from the TCP scans drop-down list. Save Changes when its done
13. Change the Profile to Xmas Scan and start scanning
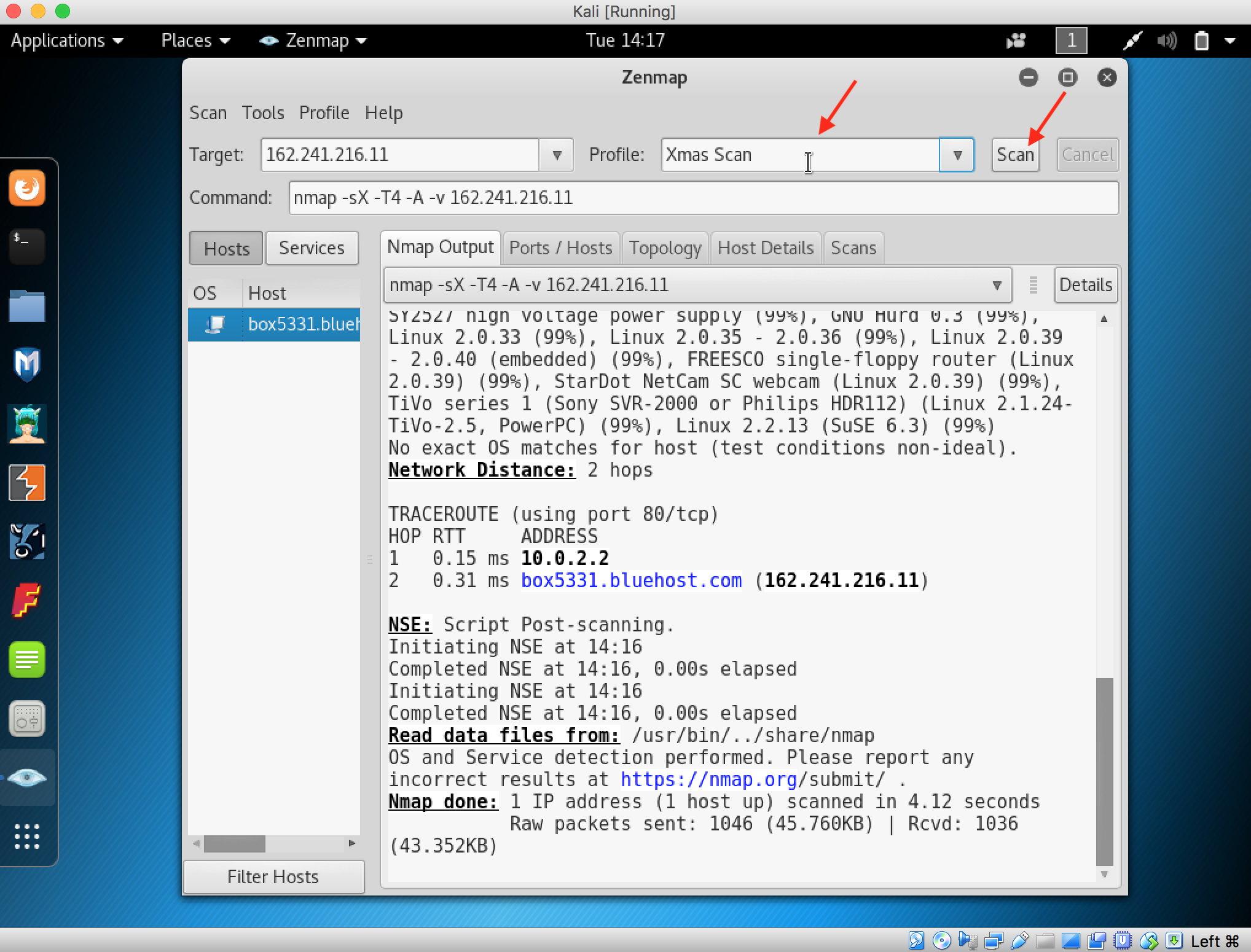
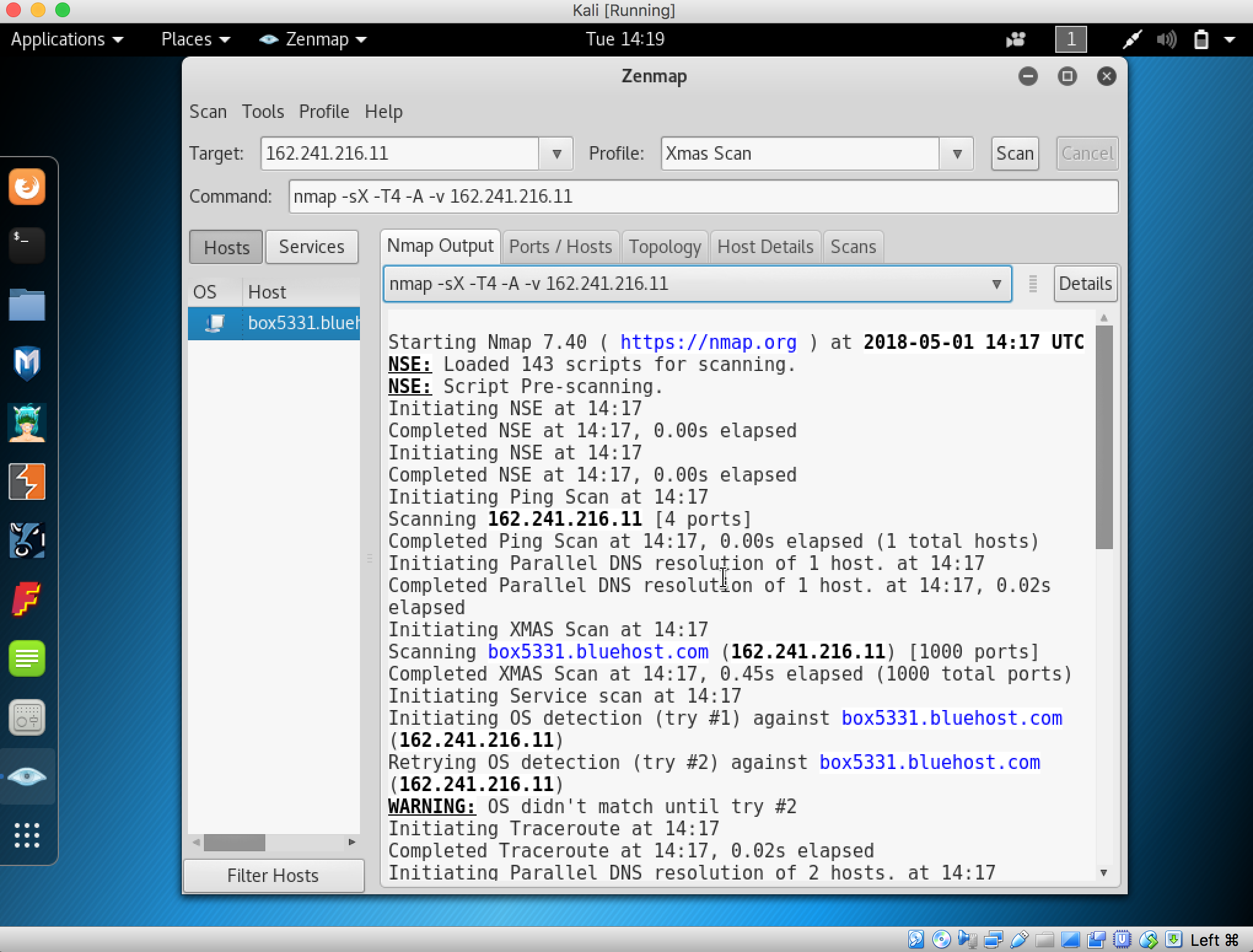
14. Nmap scans the target and shows on the Nmap Output
15. Null scan works only if the operating system’s T C P /IP implementation is developed according to RFC 793.In a null scan, attackers send a TCP frame to a remote host with no Flags. To do the Null Scan, do the same thing before by creating a New Profile and fill Null Scan in the profile name
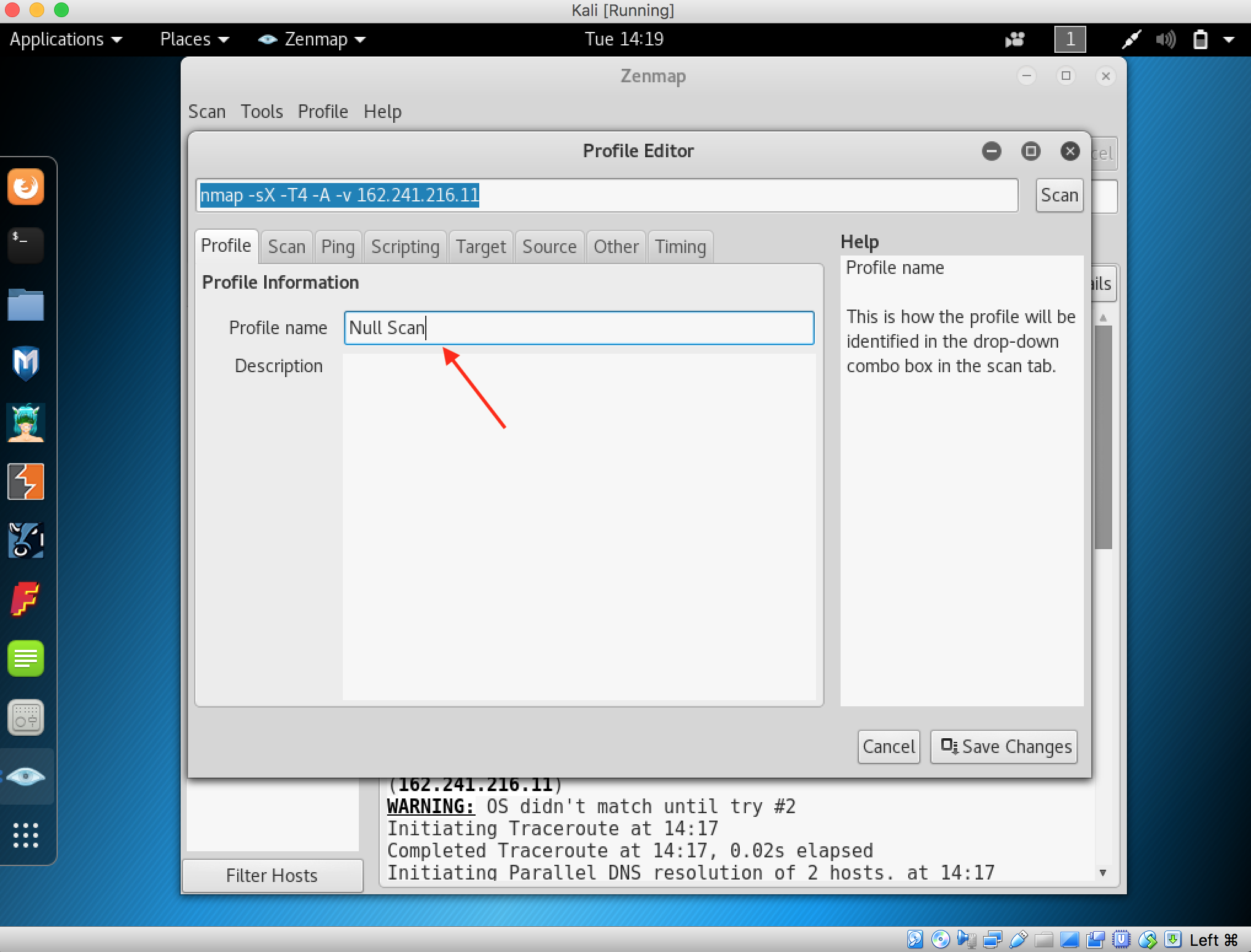
16. Click on the Scan Tab then change the TCP Scan dropdown to Null Scan (-sN), and then save changes
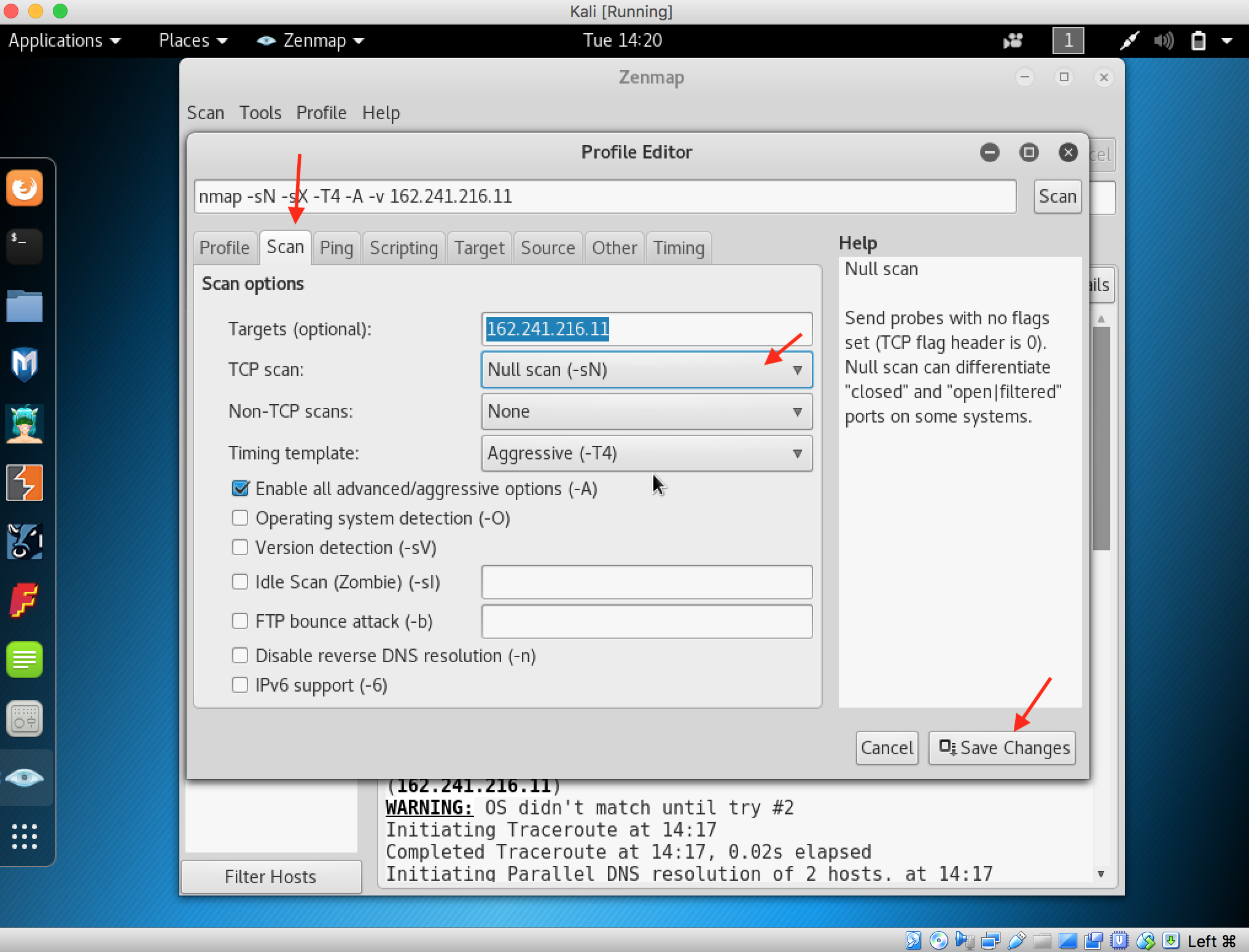
17. Perform the Null Scan by changing the profile and start the scan
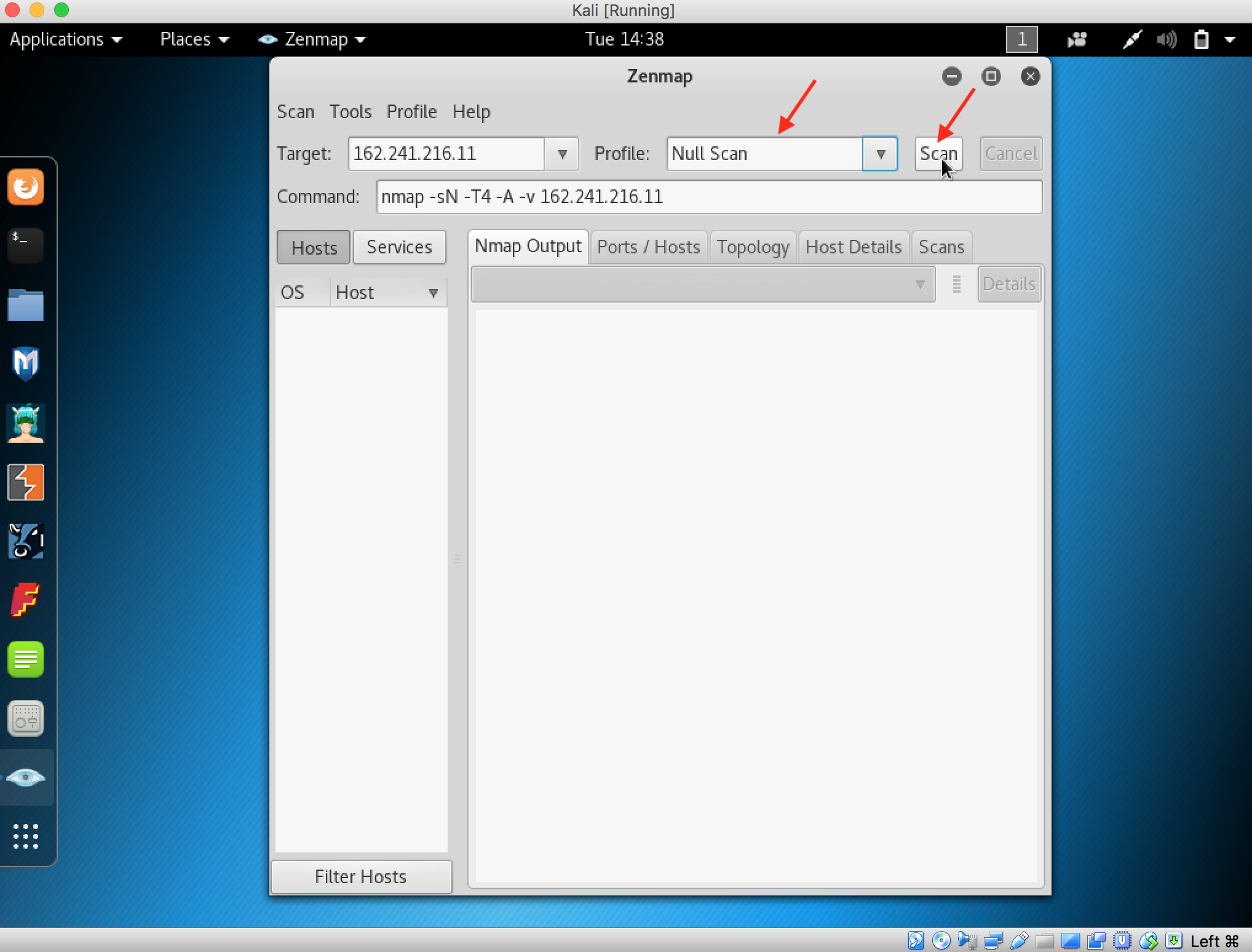
18. Nmap scans target and display result in Nmap Output
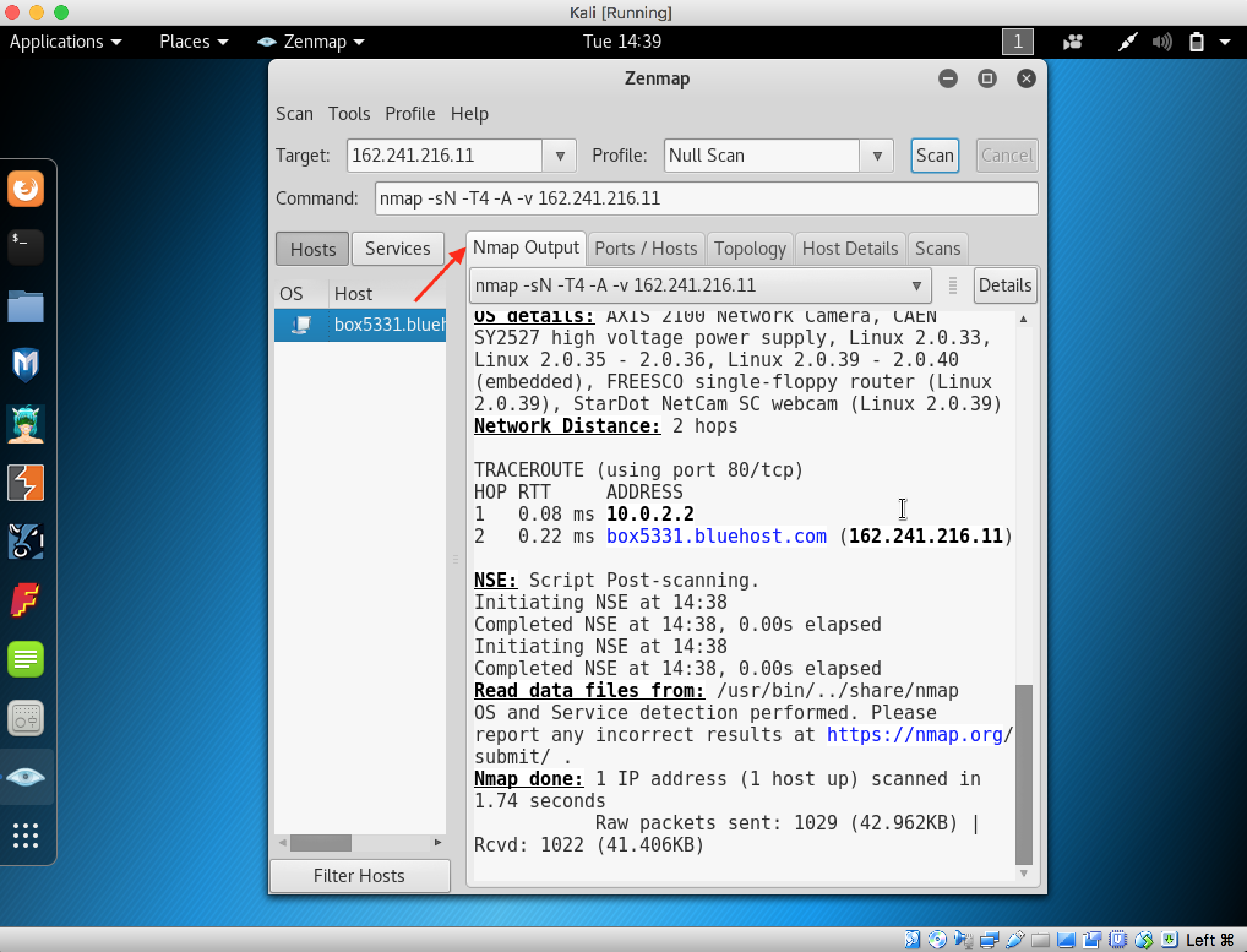
19. Click the Host Details tab to view the details of hosts, such as Host Status, Addresses. Open Ports, and Closed Ports
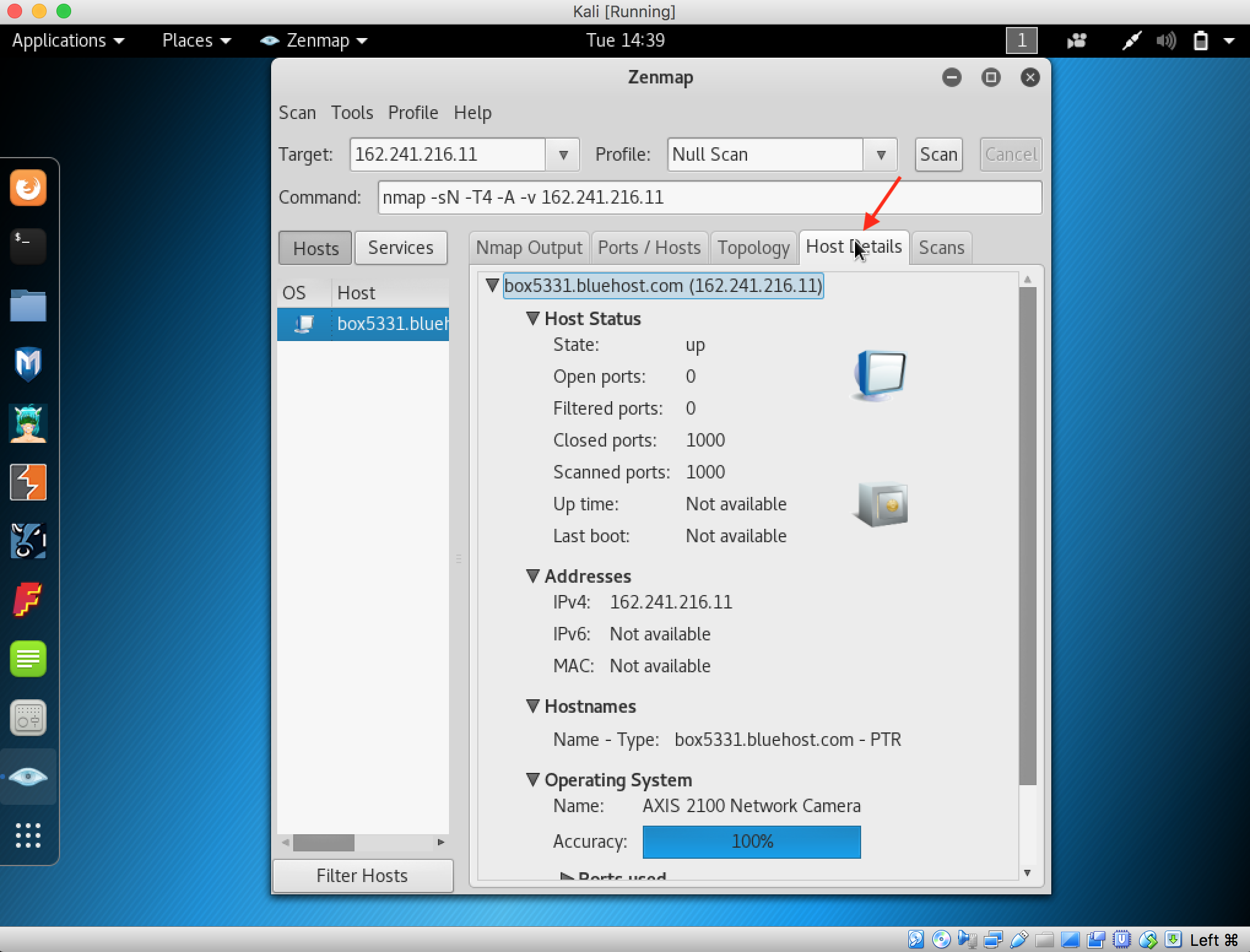
20. Attackers send an ACK probe packet with a random sequence number. No response means the port is filtered and an RST response means the port is not filtered. To perform ACK Flag Scan, create new profile. Fill the profile name with ACK Flag Scan.
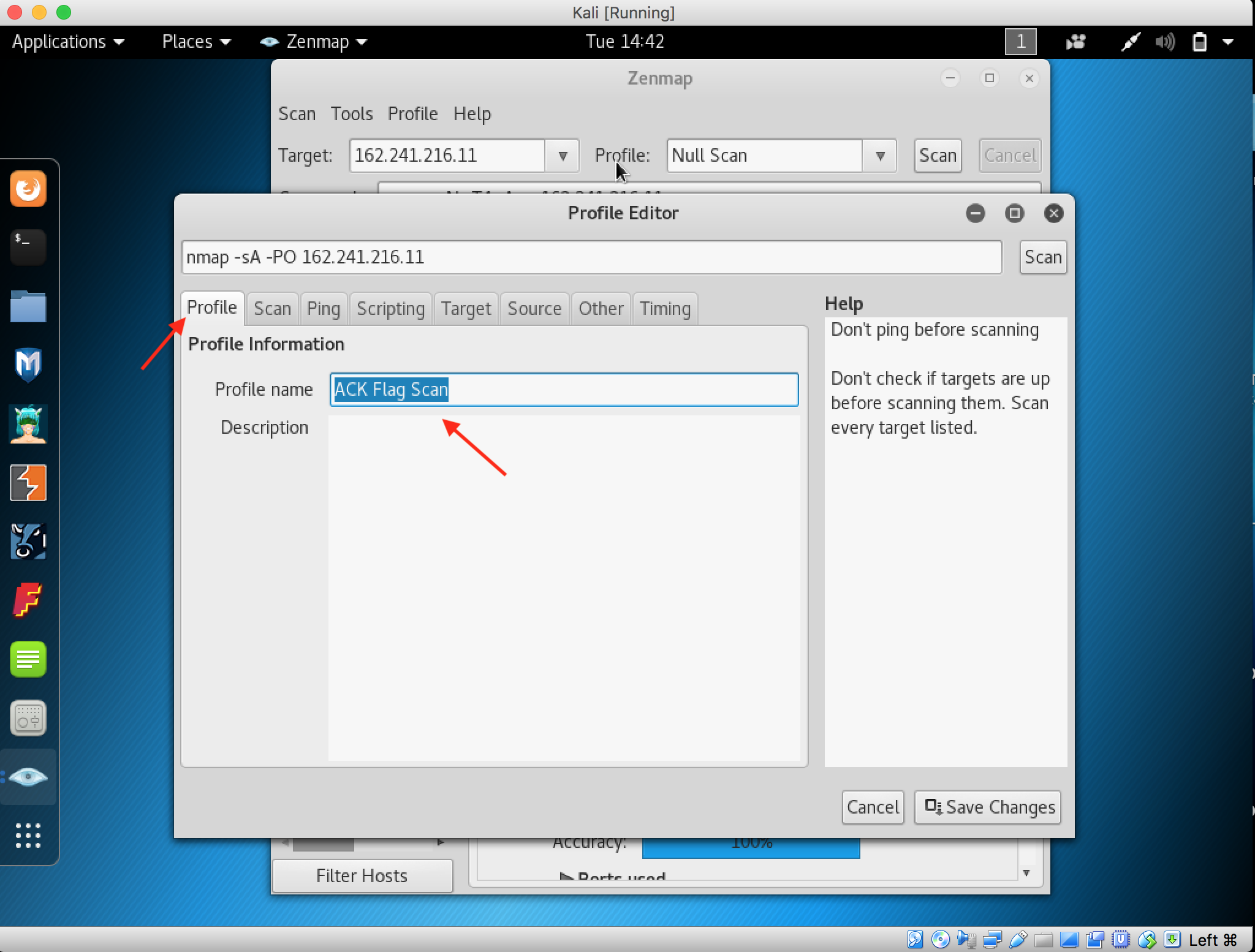
21. Click the Scans tab and change the TCP dropdown to ACK scan
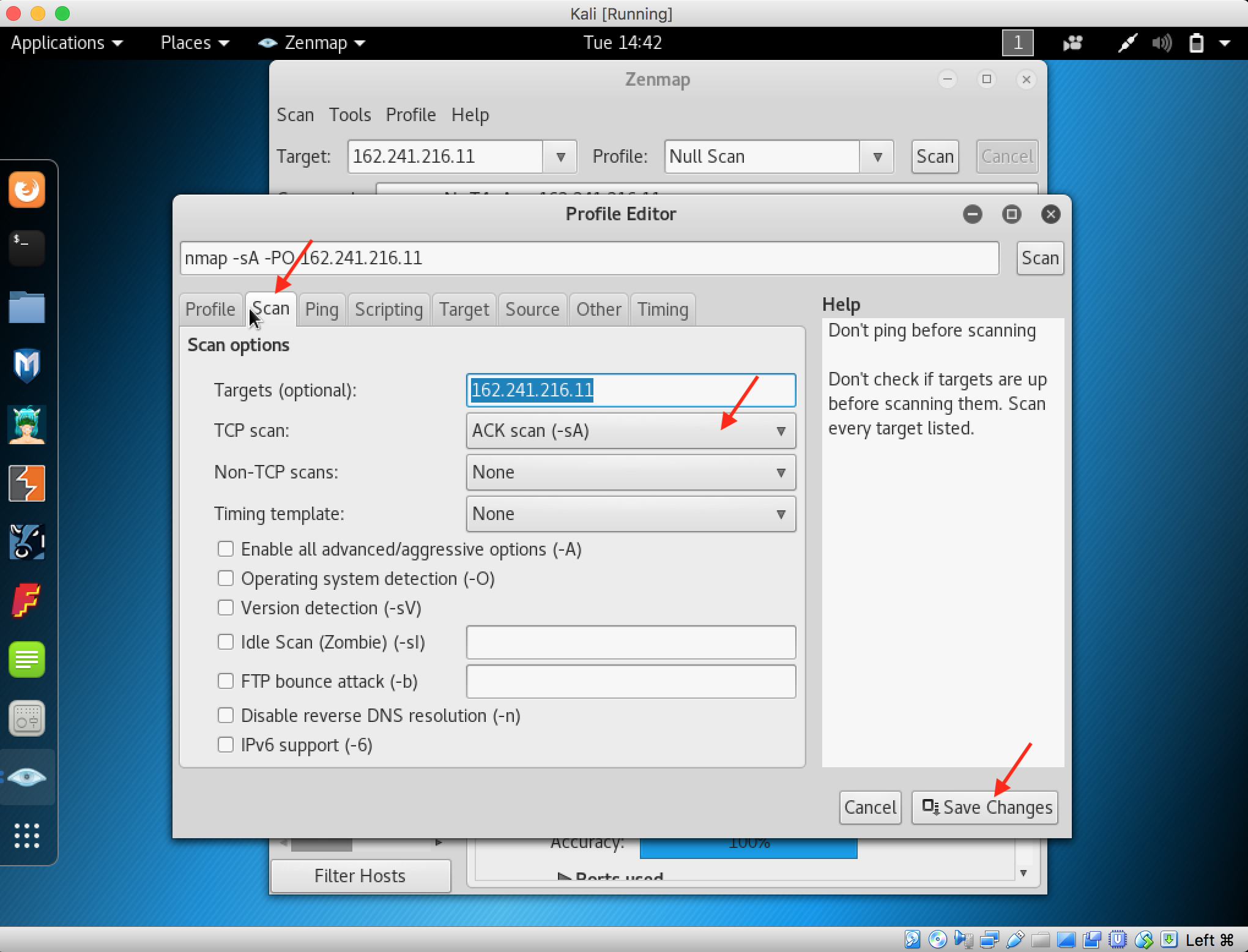
22. Click the Ping tab and check the IPProto Probes (-PO) then save changes
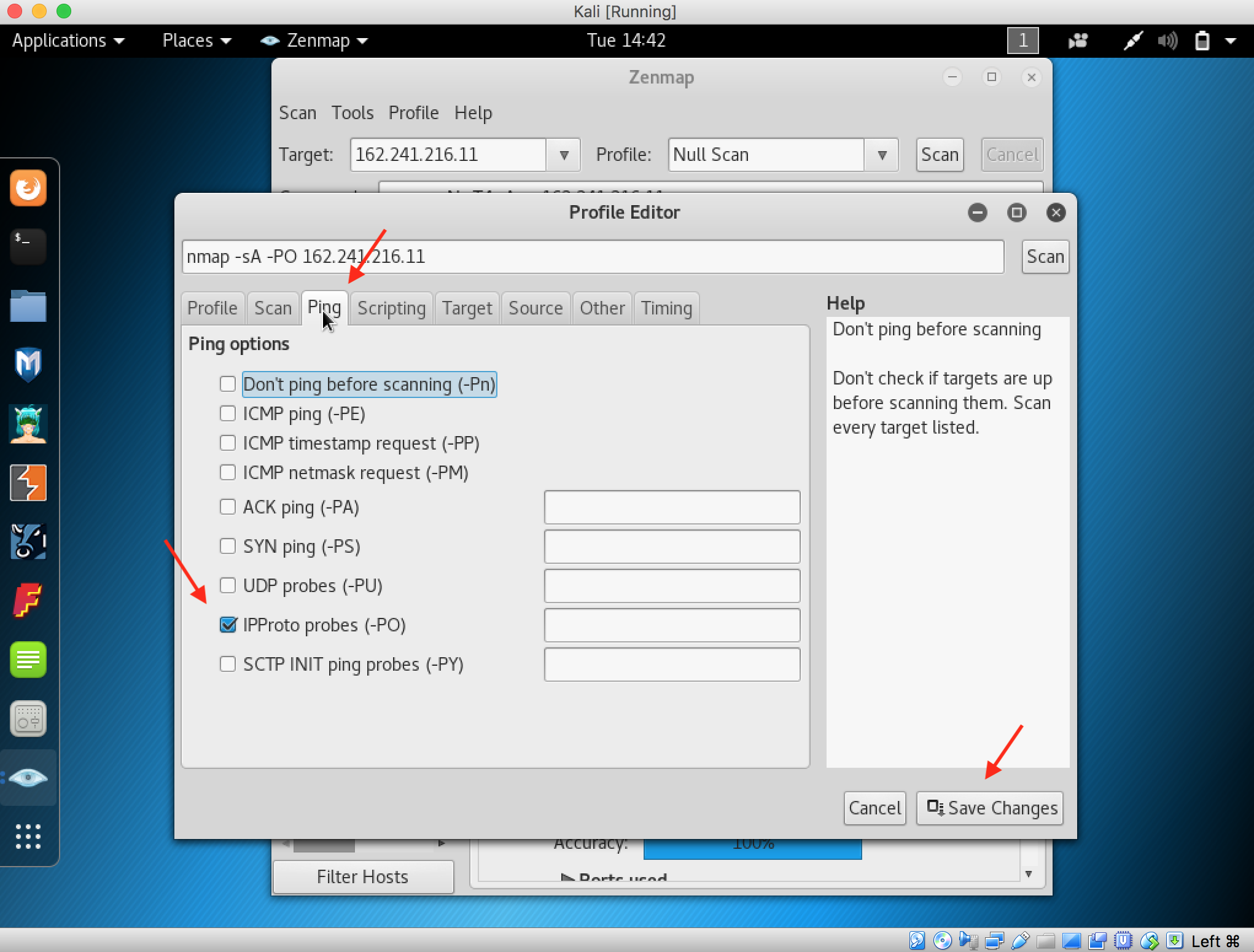
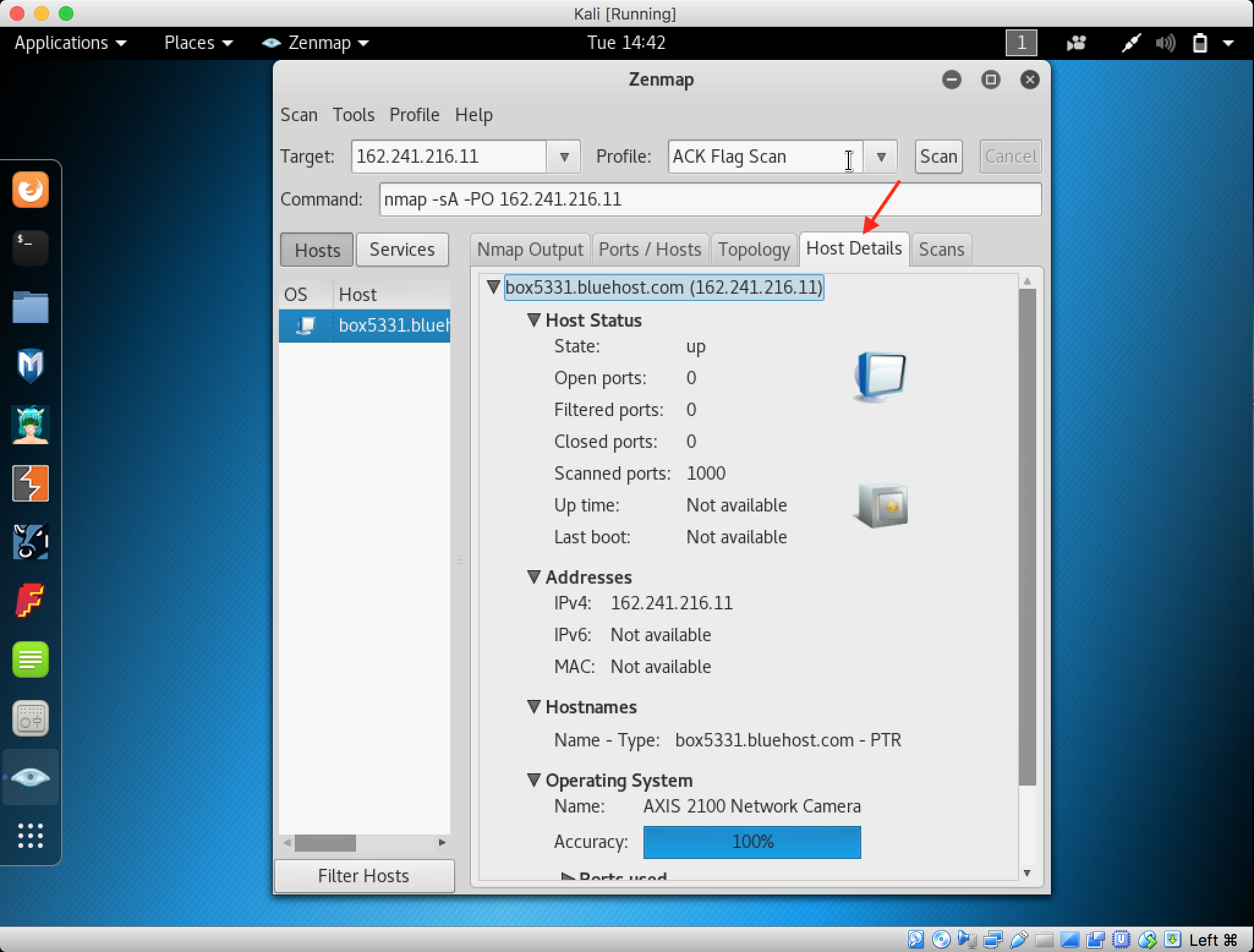
23. Start perfoming the ACK Flag Scan by changing the profile and then start the scan and here the result is shown by Nmap in Output tab.
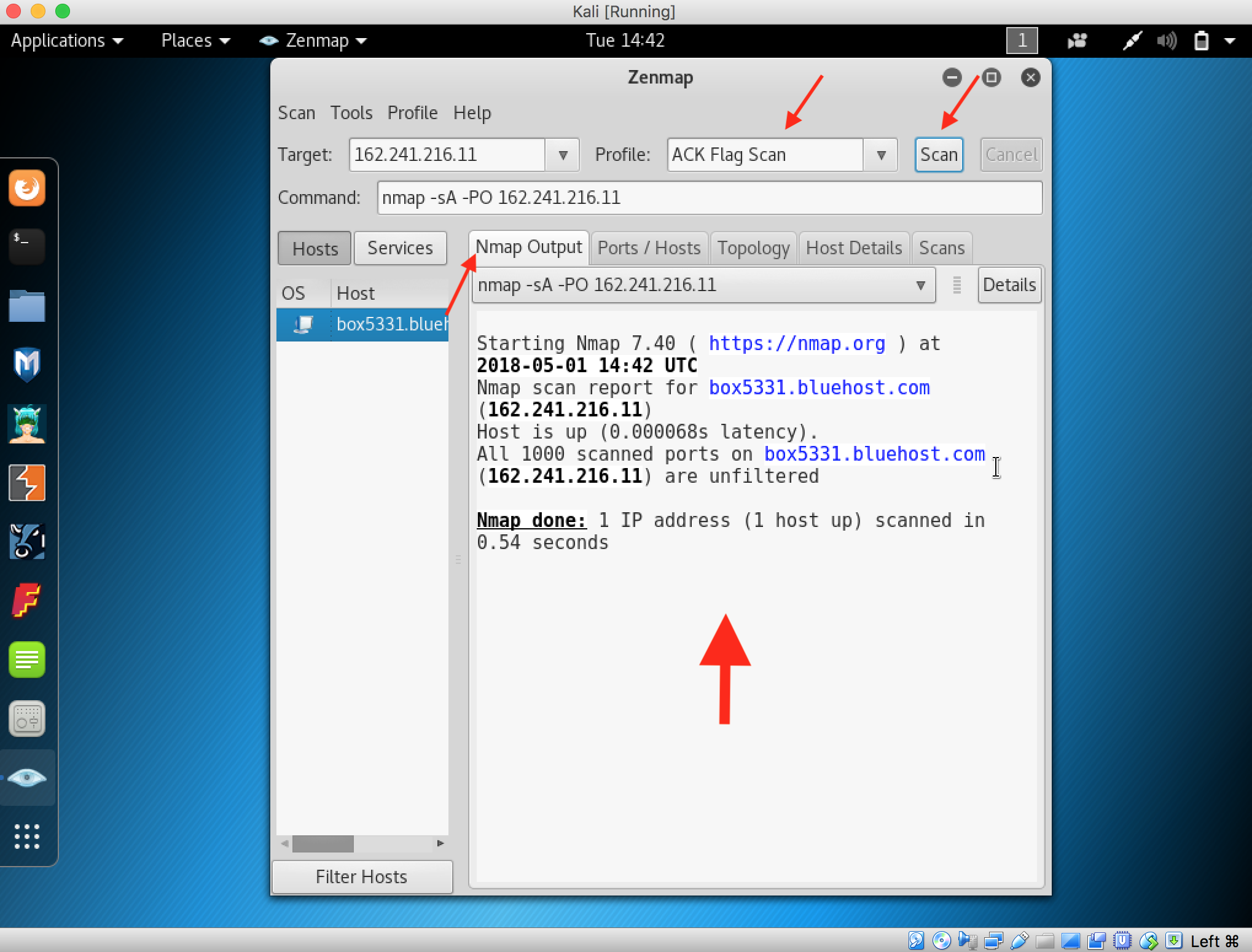
24. Click the Hosts tab to show more information regarding the hosts