Download the archive of DVWA into the apache2 folder. Rename it to make easier to find from browser.
# cd /var/www/html # wget https://github.com/RandomStorm/DVWA/archive/v1.9.zip && unzip v1.9.zip # mv DVWA-1.9 /var/www/html/dvwa
Now you need to set the permission of writing and execution to the folder.
# chmod -R 777 dvwa
Let’s start with server configuration. Start mysql to create a database and an account. Password for the root is a blank space, so just hit enter.
# service mysql start # mysql -u root -p
mysql > create database dvwa; mysql > CREATE USER 'user'@'127.0.0.1' IDENTIFIED BY 'p@ssword'; mysql > grant all on dvwa.* to 'user'@'127.0.0.1'; mysql > flush privileges; mysql > exit
# service mysql stop
DVWA requires a module for php which is not installed into Kali 2.0.
To install it you need to add a debian source for APT.
# add-apt-repository 'http://ftp.de.debian.org/debian sid main' # apt-get update # apt-get install php5-gd
Now you’re finally ready to edit the source of php config files to make sure your web application connects to the database and has got a working captcha.
Keys for captcha needs to be generated from Google service, so go here , login with your Google account and copy the two keys (public and private).
# gedit /var/www/html/dvwa/config/config.inc.php
Add user and password of the mysql database, and the keys.
There’s a screenshot on how needs to be your file after editing.
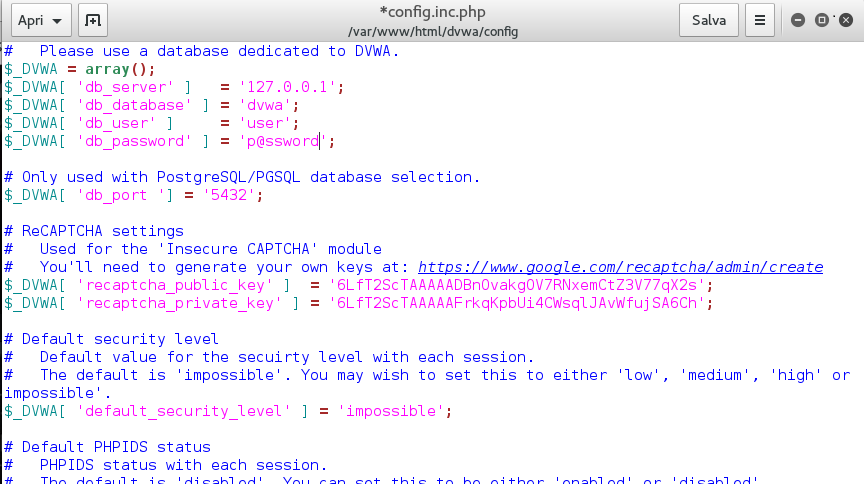
You’re almost done! Last thing to do is edit the main config file for apache2, which is not correctly overrided by the dvwa’s one.
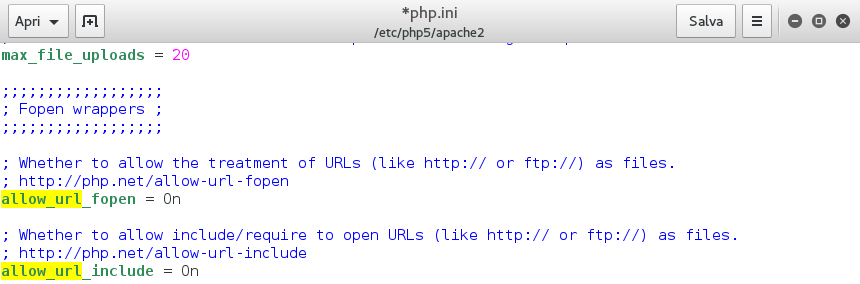
# gedit /etc/php5/apache2/php.ini
Jump to the line 821 and enable the allow_url_include. This is necessary to exploit the file upload vulnerability.
You’re done.
Your DVWA is correctly setted and can now be started.
# service apache2 start && service mysql start # iceweasel http://127.0.0.1/dvwa/setup.php
Here’s what it’s in front of you.
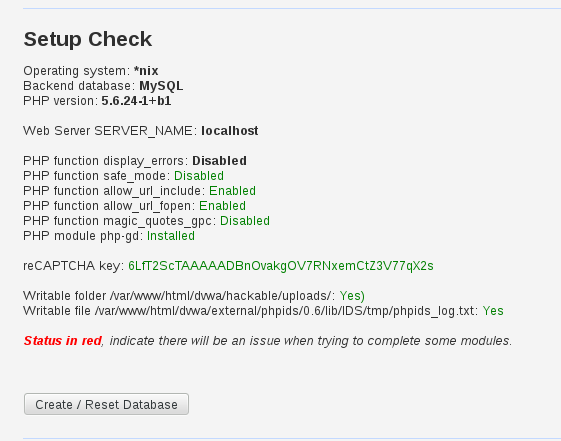
Click on “ Create / Reset Database “ .
You’ll now be redirected to the login page: insert the default credentials ( admin / password ) and log into the panel.
Here you’re able to change the strenght of vulnerabilities by clicking on “DVWA Security” .
Set the low level and began to hack!
